We often get asked how we prioritize which security patches to build. To answer, it helps to understand how risk is spread across the software supply chain. (Hint: it’s not evenly distributed.) Our research indicates that open source vulnerabilities tend to follow the Pareto principle, where just a few libraries are responsible for the majority of vulnerabilities found in customer environments.
According to the 2024 Dependency Management Report, updating the top 15 most vulnerable Java libraries can eliminate 60% of all vulnerability findings. This isn’t just a Java problem — similar patterns emerge in other languages too. In the case of the Python ecosystem, updating the top 15 components to non-vulnerable versions would remove more than 75% of all the vulnerability findings.
So why aren’t more organizations simply upgrading their open source dependencies? Why build security patches at all?
The challenges of dependency management
Let’s look to the Java open source ecosystem for an example. Modern Java applications heavily rely on open source libraries, like Spring Boot. One common dependency in Java libraries is jackson-databind, a widely-used Java library for serializing and deserializing JSON data. Its popularity and versatility also mean it's incorporated as a dependency into other Java libraries, like Spring Boot. In this scenario, jackson-databind is a transitive dependency (That’s a dependency of your dependency).
The trouble with tribbles, ahem we mean transitives
When you attempt to upgrade jackson-databind, you need to ensure compatibility with your original dependency (such as Spring Boot) and any other direct or transitive dependencies that use it. Any changes in how the dependency works may require application developers to make changes to their own code.
Of the 254 Java libraries we analyzed, each had an average of 14 transitive dependencies. Even if your application uses just 7 libraries, you likely have around 100 transitive dependencies. As we’ve discussed previously, upgrading transitive dependencies is especially thorny. While you can force an update on a transitive, it’s often a very bad idea for a few reasons:
- You can have multiple different versions of the same dependency in your application
- It’s harder to see what parts of a transitive dependency are actually being used
- Forcing updates creates maintenance challenges every time you update the direct dependency
Once you fix one issue from a transitive upgrade, you discover another, and another, multiplying across your codebase. Before you know it, you're buried in a pile of compatibility problems that seem to multiply exponentially.

This is the trouble with transitives: security upgrades lead to breaking changes, costing developers time and effort spent on research, validation, fixing, and testing. In fact, we’ve found that 95% of open source version upgrades contain at least one potentially breaking change. Tackling upgrades requires careful prioritization and a smart strategy to prevent your fix from turning into a cascade of breakages.
Answer: fix the few to secure the many
To answer the original question: Endor Labs prioritizes building patches for the few open source libraries that are responsible for the majority of critical and high vulnerabilities. Ultimately 95% of vulnerabilities are found in transitive dependencies, and they tend to hang around in customer environments due to the complexity of upgrading. By focusing on these concentrated risk points in the software supply chain, we can improve overall security.
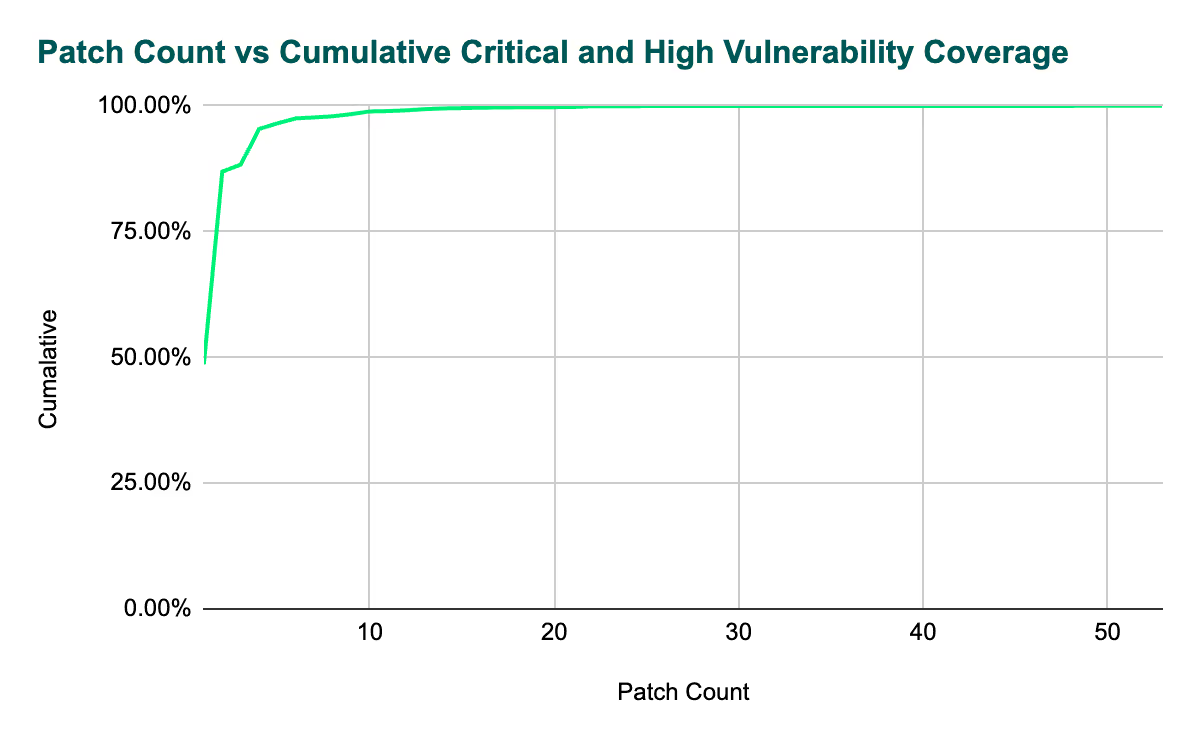
To give an example, one financial services customer found they could remediate 35,000 critical and high vulnerabilities using Endor Patches. In most organizations, a few open source packages account for the majority of vulnerabilities—and this case was no different. In total they had 10,000 critical and 25,000 high vulnerabilities (reachable or unreachable) that could be fixed with Endor Patches, with their largest namespace accounting for 22,000 of those vulnerabilities. After investigation they determined that using just nine Endor Patches would help them remediate 98.35% of their critical and high vulnerabilities in that single namespace.
Fix vulnerabilities without breaking changes
At this point you might be wondering how this all works.
Fundamentally, Endor Labs takes a different approach than other AppSec tools you might be familiar with. We think your SCA tool should do more than show you problems: It should also give you solutions. Through program analysis, we analyze your applications at a function level to understand how dependencies and transitives are called so that you can:
- Identify real risk that could be exploited in your applications based on which dependencies (direct and transitive) are reachable in your code.
- Prioritize upgrades based on the likelihood of breaking changes using upgrade impact analysis.
- Get safe immediately by patching vulnerabilities with Endor Patches.
Endor Patches are a way to remediate risks by working smarter, not harder. You can quickly patch hard-to-fix transitive dependencies now, and worry about upgrading when your software engineering teams are ready to pick up the work. Read our whitepaper to learn more about how we build and test Endor Patches, and how to deploy them yourselves – no email required!
If you’re ready to take action, book a demo to see how Endor Labs can help you fix the few and secure the many with upgrade impact analysis and Endor Patches.
40+ AI Prompts for Secure Vibe Coding



What's next?
When you're ready to take the next step in securing your software supply chain, here are 3 ways Endor Labs can help: