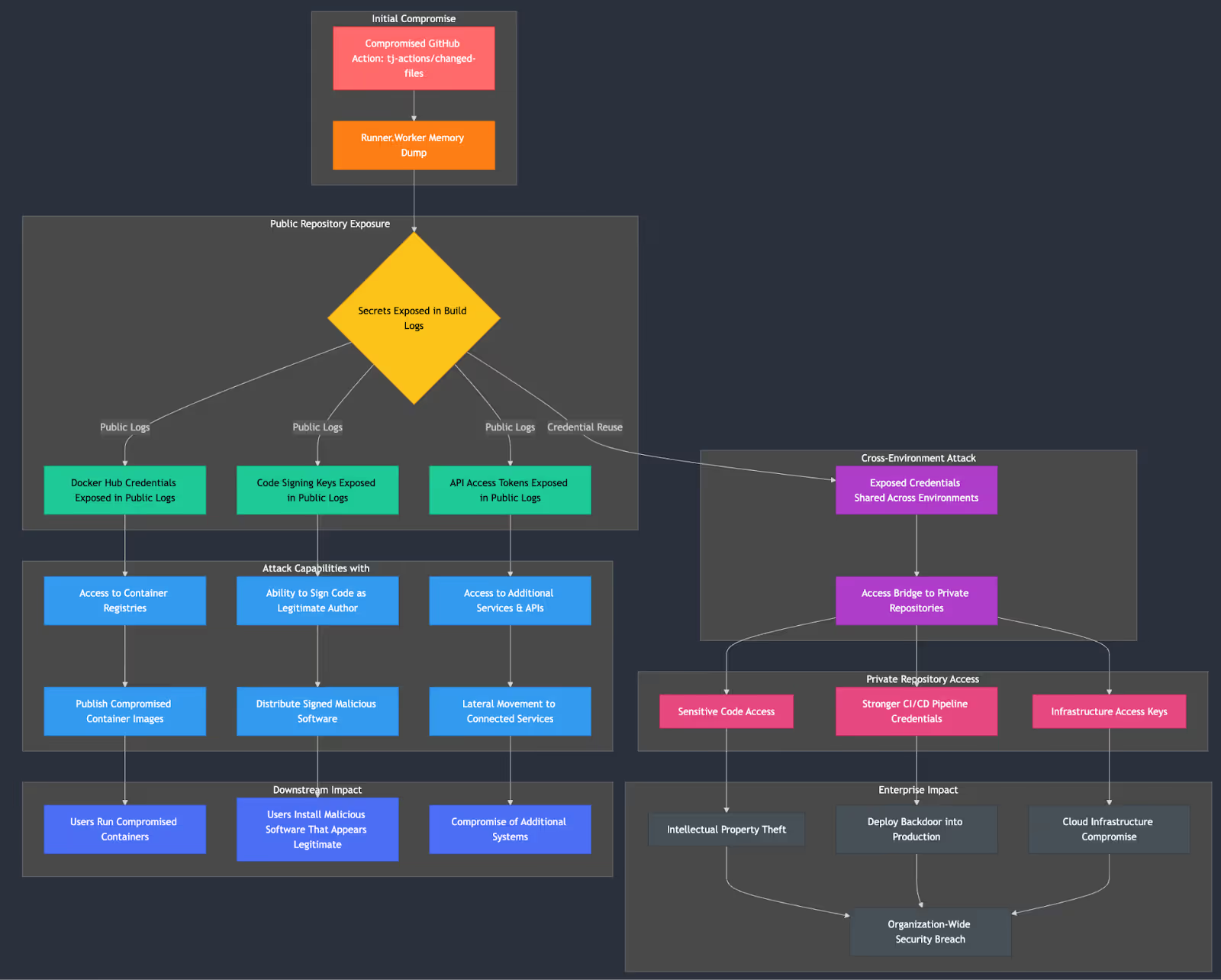
Yesterday, a malicious commit was discovered in the popular tj-actions/changed-files GitHub Action, which is used in over 23,000 repositories. The attackers modified the action’s code and retroactively updated multiple version tags to reference the malicious commit. The compromised Action now executes a malicious Python script that dumps CI/CD secrets, impacting thousands of CI pipelines.
This blog post provides our assessment of the impact and guidance for Endor Labs customers, as well as general recommendations for anyone impacted.
Affected versions
CVE-2025-30066 covers the incident. This CVE impacts public GitHub repositories with GitHub Actions enabled. All versions were impacted. GitHub has removed the Action and users must find alternative implementations. This means that CI pipelines using the compromised Action could crash unless you are using a cached version.
This currently impacts public GitHub repositories with GitHub Actions enabled, but we’ll want to keep an eye on downstream open source packages and containers in the coming days.
Update March 17, 2025: GitHub has since restored the tj-actions/changed-files repository. None of the versions include the malicious exploit code anymore.
Impact to public Github repositories and open source projects
The attacker was likely looking to compromise the software supply chain for other open source libraries, binaries, and artifacts created with this. Any public repository that creates packages or containers as part of a CI pipeline could have been impacted. That means potentially 1,000s of open source packages have the potential to have been compromised.
This can also apply to enterprise organizations that have both private and public repositories. If these repositories share CI/CD pipeline secrets for artifact or container registries these registries can be potentially compromised.
We have no evidence that any downstream open source library or containers has been impacted at this time. But we urge open source maintainers and the security community to join us in keeping a close eye out for potential secondary compromises.
Guidance for Endor Labs customers
To ensure they are not impacted, Endor Labs customers should:
- For customers using the Endor Labs Github App: search your dependencies
- For customers using CI or CLI scanning: configure CI scanning
- Audit GitHub logs for suspicious IP addresses
- Rotate any active secrets in their repositories
1) For customers using the GitHub App: search your dependencies
The easiest way to find if you’re impacted is to go to the Dependencies in the Endor Labs dashboard and search for a dependency with the name tj-actions/changed-files. This will immediately show you the impacted projects and CI pipelines:
2) For customers using CI: use the CLI to configure scanning
If you haven’t enabled CI scanning in Endor Labs, you must scan your repos by adding the parameters --ghactions --secrets --git-logs to your configuration, in addition to the parameters you’re already using. This will discover all the repos that have been affected.
3) Audit GitHub logs for suspicious IP addresses
If you found that you were using tj-actions/changed-files, you should review your GitHub logs for suspicious IP addresses. You can find your GitHub Actions logs under your organization account settings. GitHub has instructions on how to review your logs for suspicious IP addresses.
4) Rotate any active secrets in their repositories
If you were using tj-actions/changed files, it might have compromised access to your repositories. That means if your repos had secrets, these might have been leaked as well. You should immediately disable any active secrets from these repos and replace them.
If you’re not using Endor Labs, here’s what to do
If your organization uses GitHub Actions, you should take the following steps immediately to determine if you are impacted by the tj-actions/changed-files compromise:
- Find out if you’re impacted
- Remove tj-actions/changed-files
- Audit past CI workflows for signs of compromise
- Rotate any exposed secrets
1) Find out if you’re impacted
Inspect your GitHub Actions workflows to see if tj-actions is in your codebase. The easiest way to do this quickly is to run a search. Replace [YOURORG] with your organization's name on GitHub: https://github.com/search?q=org%3A[YOURORG]+uses%3A+tj-actions%2F&type=code
Note that this approach is not perfect, and looking in your codebase is not enough. You can still have actions or workflows that import other actions (i.e. as transitive dependencies).
2) Remove tj-actions/changed-files immediately
GitHub has removed tj-actions/changed-files. This means any CI pipelines currently using it will break. You should remove it and consider an alternative. Keep in mind that removing it from the main branch of your repository isn’t enough—depending on your action configurations, it could still run on other branches. To ensure it's fully removed, delete it from all branches.
Alternatively, GitHub offers a feature that allows you to create an allowlist for GitHub Actions, ensuring they won’t run even if they remain in your code.
3) Audit past CI workflows for signs of compromise
Check logs for suspicious outbound network requests. Prioritize repos where your CI runner logs are public, as secrets are dumped to stdout in the payload.
4) Rotate any exposed secrets
Disable and rotate any secrets that were stored alongside your repos.
Additional Resources
40+ AI Prompts for Secure Vibe Coding



What's next?
When you're ready to take the next step in securing your software supply chain, here are 3 ways Endor Labs can help:










