Security engineers often find themselves in a tough spot. You need developers to get things done, but their priorities lie elsewhere. They’re busy building features, fixing bugs, and shipping code, and they sometimes feel like security is in the way. It's not that they don’t care—they do. But security is usually not the first thing on their mind (or the fourth in many cases). We won’t go into security’s economic incentives.
The challenge is finding a way to make security a natural part of the process without adding unnecessary friction. It's a constant balancing act: How do you get developers to care about security without feeling like you're just piling on more work? This is the paradox of application security that every security team must manage.
Gaining buy in from your security partners – in this case, software engineers – follows a predictable maturity staircase.
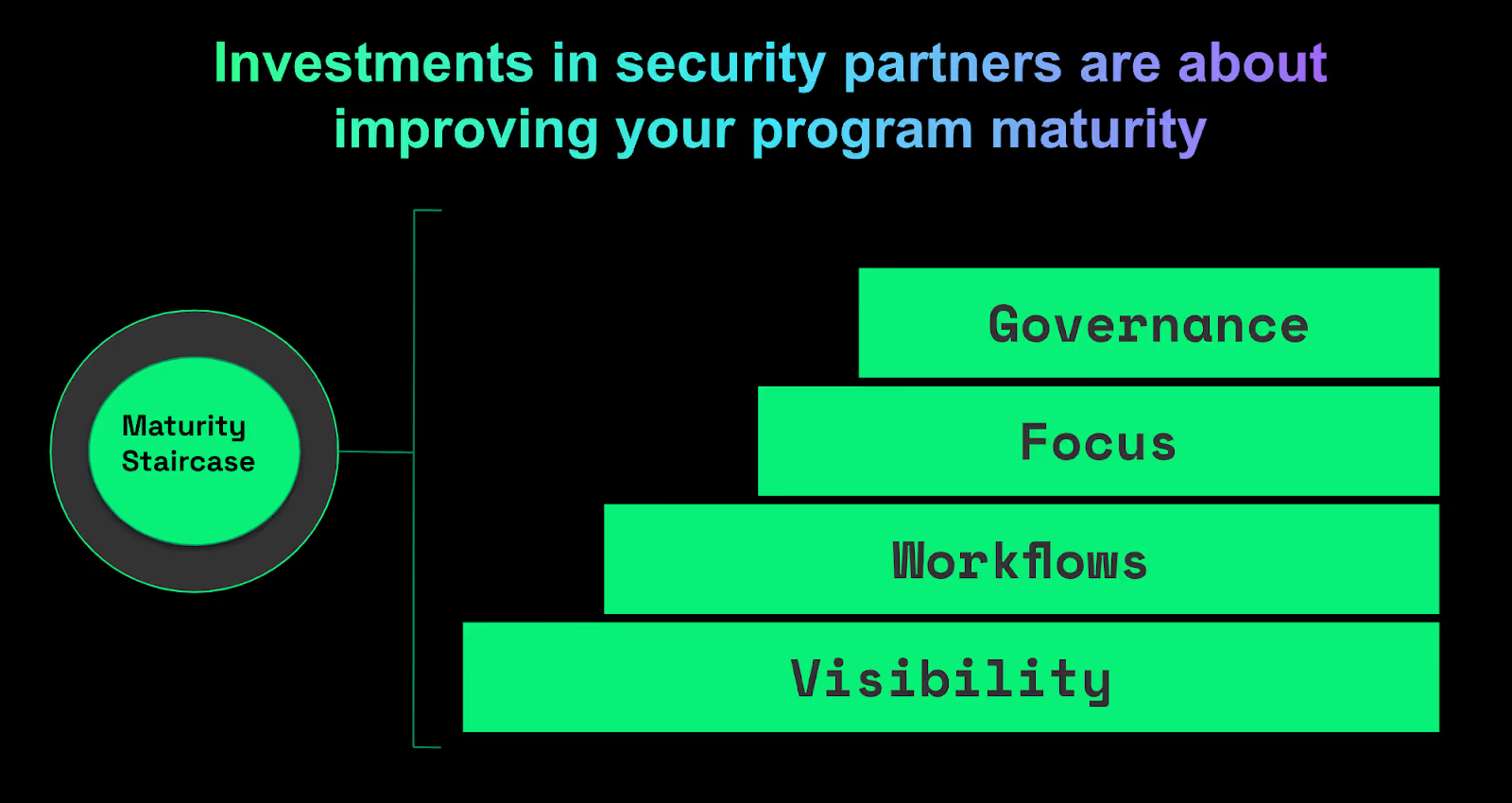
So what is the secret? Climbing the Maturity Staircase with speed—and at Endor Labs we’re giving you rocket boots to climb that staircase quickly and effectively. Let's break down how your program can climb the staircase, one step at a time.
Step 1: Visibility – See the whole picture from the start
The foundation of any AppSec program is visibility. If you don’t know what’s in your environment, you’re flying blind. But it’s not about seeing everything—it’s about seeing what matters. You don’t want to overload yourself (or your dev teams) with noise; you need clarity on the things that could actually cause harm.
To start, you need an accurate software inventory (software bill of materials, or SBOM) to know what you’re assessing in the first place. An accurate SBOM requires knowing the exact version of your software runtime (like JDK 11 or Python 3.7) and your package manager (like Gradle 7) at the time of the build or installation.
Without this context, you could be chasing phantom risks because the bill of materials may change. You can solve this by integrating scanning tools directly into the same environment as your build tools. But what if your team isn’t mature enough to have reusable CI templates set up yet? What if you can’t take the time to perform several CI integrations without introducing friction?
You still need to identify::
- What’s the risk in my environment?
- What software assets do I have, and which are critical?
- Where should I focus first?
Most teams don’t start with a perfect asset inventory. That’s fine—it’s about knowing enough to get started. As you gain more visibility, you'll be able to justify that next step with leadership.
“I have all these problems and I need to figure out what to do with them!”—this is your ticket to getting buy-in to improve your asset inventory and collaborate with developers more closely. After all, management will want you to focus your time on the highest value applications and if you don’t know what those are or who to contact then you might not be spending your time as effectively as you could.
Get an accurate SBOM
Endor Labs takes the friction out of maintaining an accurate bill of materials. With seamless integration into GitHub, GitLab, and Azure Repos, you can quickly see the risks in your software portfolio. Our automated build tool detection identifies the correct runtime and package manager versions during scanning. When automated detection isn’t possible, you can use scan profiles to define the necessary tooling. This eliminates the need for complex CI integrations upfront, allowing your team to move quickly while staying accurate. For teams without mature platform engineering setups, this is a game changer. You get the right information, faster, with less dependency on developer time.
Step 2: Workflows – Time to get sh*t done
Once you’ve established visibility, the next step is to take action. But getting developers to focus on security isn't easy. You’ll be successful if you can build workflows that integrate into where developers already work. Do this by starting small, gaining momentum with a few teams, and then scale up.
But you’ve got technical debt, new vulnerabilities, and legacy code riddled with issues. Prioritizing what to tackle first is key, especially when time and resources are tight. And while integrating security into CI pipelines might seem ideal, it’s not always realistic for every team. You don’t need perfect CI integrations to start addressing risks—just the right workflows.
Integrate into developer workflows
Endor Labs helps simplify the process. Our GitHub App integrates with your developers existing workflow, automating pull request scanning without the friction of a CI integration. Even without deep CI integrations, you can still detect issues early, correct them fast, and keep moving forward. You can stop worrying about getting every little piece of the pipeline in place before taking action—Endor Labs lets you start now and improve as you go.
With Endor Labs, you can scan every pull request and flag new risks immediately, without burdening developers with past debt. When a developer introduces a new risk, you can surface a warning on the pull request or even break the build to let them know that something is wrong that they introduced.
When you’re ready, you can set up security tooling in CI or integrate them into your ticketing and messaging systems. You can do this with individual teams who are more mature as a starting point. You can even alert the security team to issues so they know when the next CVE comes out and can escalate it.
Then you can start chipping away at the mountain of technical debt (or hill if you are small or very lucky). But technical debt is where focus matters because without focus you create friction.
Step 3: Focus – Spend Time Where It Matters
Now that you’re identifying and fixing issues, the next challenge is focus. Not every vulnerability is a fire drill, and not every bug needs immediate attention. Overloading your devs with a long list of issues is just going to make them tune out.
If you want to handle a mountain of tech debt, the only practical way at scale to do so is to prioritize. If you overwhelm teams with a giant mountain of potential issues to fix within a 30 day SLA - that's the fastest way to lose your credibility quickly in your organization. This is also what we’ve done historically as an industry.
This is where prioritization comes in. You need to focus on what's actually reachable, what’s critical, and what’s going to give you the most bang for your buck. By cutting down the noise, you help your developers see that security doesn’t have to be a blocker—it can fit into their workflow in a way that makes sense.
How Endor Labs helps:
Our reachability analysis helps you zero in on the vulnerabilities that are truly exploitable in your application. Nobody likes chasing down issues that don’t pose a real threat.
Using Endor Labs’ function level reachability analysis, you can identify where your application does and does not use the vulnerable function associated with a known vulnerability with the evidence to convince your development team that the issue truly merits their attention. Unlike bugs that show user impact, vulnerabilities unless actively exploited show problems that potentially exist, which makes it difficult to get buy-in to work on them without citing “compliance obligations” or “policy” to which they often, sometimes begrudgingly, will. With reachability analysis, you get the proof you need to show it merits their time and attention to approach these conversations more credibly.
What happens if you ask a team to do work and it requires them to refactor a large portion of their code? What if there is an API breaking change associated with a software update? No more are you stuck swinging the stick or asking for an ETA for an ETA for an ETA. Endor Labs enables your team to identify breaking changes associated with the version upgrades needed to fix known vulnerabilities in software components. This way you can set better expectations about the level of effort with your team. This enables the security team to have return on investment conversations rather than “fix the finding” conversations.
Finally, for those issues that haven’t proven to be as difficult, Endor Labs allows you to submit automated pull requests through a GitHub app to remediate issues based on the risk in terms of vulnerabilities and the risk in terms of operational overhead to fix something. By identifying breaking changes and potential remediation risk you can start to get what can be easier and more important in front of your development teams without overwhelming them with pull requests.
Finally, ever tried bumping a dependency version only to find you need to upgrade your Java version too, which leads to a complete refactor—cough damn you Spring cough— ? That’s where Endor Patches come in. We provide minimal viable security patches where the vulnerability is backported for you. This helps you to patch the risk without breaking everything—saving you and your devs countless hours of frustration.
Step 4: Governance – Improve a little every day
Finally, at the top of the staircase, you’ve got governance. This is where it all comes together. Good governance means you’re focused on continuous improvement and you have an established program. Now the question becomes, how do you improve next!
How Endor Labs can help:
Our flexible policy engine allows you to set rules and policies that align with your program’s maturity level, and we help you adjust those policies as you grow.
If you want to focus on the low hanging fruit or the highest risk systems, you aren’t alone. Endor Lab’s policy system was designed to help you start from any level of maturity
You can configure CI warnings, pull request comments and your ticketing and messaging workflows for what matters most to you right now. If you’re just starting, maybe you are only focused on remediations for critical vulnerabilities that are reachable at the function level of your code so you don’t overwhelm your team. But as you grow, you inevitably graduate and when you graduate you need a path to change to always improve.
Policies can apply differently to different teams or be improved over time to be more strict as you tackle the technical debt throughout your organization.
Climb the AppSec Maturity Staircase with Confidence
Each stage of this maturity staircase represents a critical aspect of your security program’s evolution, and Endor Labs isn’t just a tool you use—it’s your escalator to the top. We don’t just give you the tech; we give you the flexibility, speed, and focus to mature faster without sacrificing quality or burning out your developers.
Endor Labs ensures you get value right away:
- Visibility means you see what matters instantly.
- Workflows keep things smooth as you ask teams to do work.
- Focus lets you be more productive as a team and not lose friends.
- Governance helps you grow as you mature over time.
No one ever said climbing the maturity staircase would be easy — working with humans never is (machines just talk back a lot less) – but we can make it a lot less painful.
We’re here to help – book time with us to learn more about how we can help evolve your application security program together.
40+ AI Prompts for Secure Vibe Coding



What's next?
When you're ready to take the next step in securing your software supply chain, here are 3 ways Endor Labs can help:








.png)