A brand-new critical CVE landed today that targets WebDriverManager (docs found here) — the popular open-source helper library that automatically downloads and wires browser drivers for Selenium tests.
If your Slack channels just lit up, take a breath. Most organizations will never see this issue in production.
The headline, in plain English
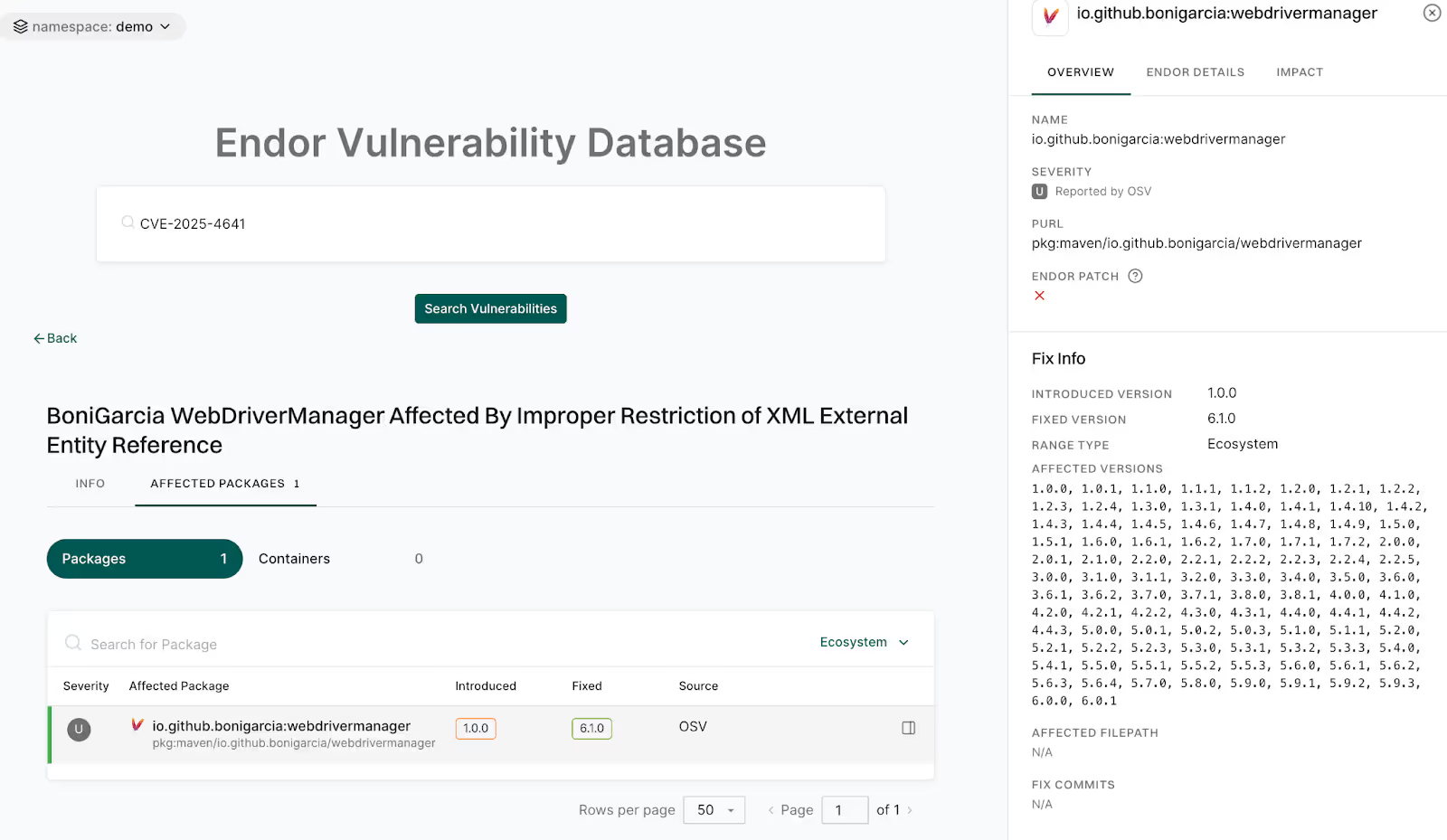
- Vulnerability: Improper Restriction of XML External Entity Reference (XXE) in WebDriverManager.java
- Affected versions: 1.0.0 → 6.0.1 (fixed in 6.1.0)
- EPSS score: 0.06 % → extremely low probability of exploitation in the wild, but this can change
- Typical usage: Browser automation and UI test pipelines, not production runtimes
- Attack surface: Only exploitable when a test or pipeline allows WebDriverManager to reach an attacker-controlled host
Why this looks scary at first glance
XXE vulnerabilities can, in the worst case, expose files or enable SSRF attacks. Combine that with the “critical” CVSS label and it’s understandable to feel uneasy.
But CVSS never tells the whole story. The real-world risk hinges on two questions:
- Is the vulnerable code even reachable in my environment?
- Can an attacker realistically control the host WebDriverManager calls?
For the vast majority of teams, the answer to both is “no.”
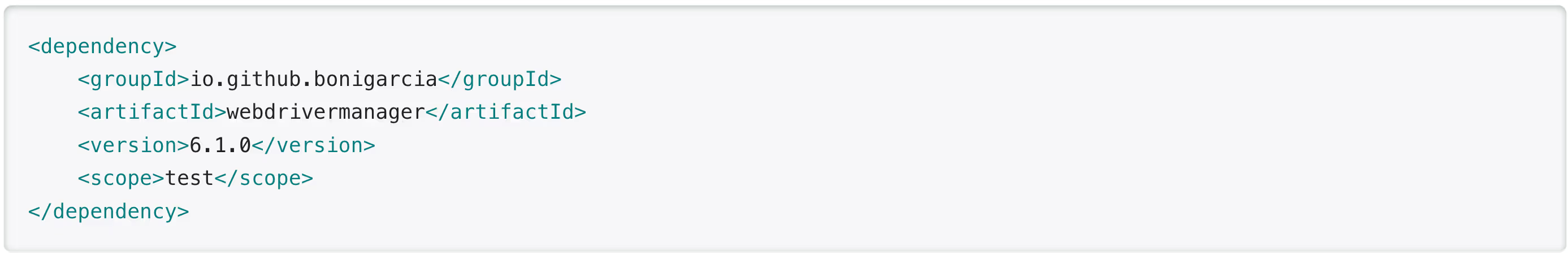
- WebDriverManager is a test-only dependency. Your production services (the ones that handle live data) typically never ship its classes. See how the documentation recommends to declare it using the test scope):
- CI runners rarely talk to untrusted networks. They pull drivers from the official mirrors WebDriverManager points to by default; an attacker would need to hijack DNS or trick the tool into fetching from their own server.
What to do right now
- Confirm your version. Scan every repo and container image for webdrivermanager below 6.1.0.
- Upgrade to a safe release. Move directly to 6.1.0, or at minimum 6.0.2, to close the XXE issue.
- Lock down CI traffic. Ensure build runners can reach only trusted download domains, blocking outbound calls to unknown hosts.
- Watch the dashboards. Endor Labs will refresh reachability data within 24 hours, auto-clearing any findings that prove unreachable.
How Endor Labs customers are covered
- Immediate inventory impact – As soon as the CVE dropped, projects using vulnerable WebDriverManager versions were flagged and customers made aware (and in this case told mostly not to panic).
- Reachability update – Within the next 24 hours our call-graph analysis will mark the finding reachable only if your test code actually invokes the vulnerable XML path, eliminating false positives.
- Upgrade Impact Analysis – If they do choose to upgrade, users will jump from 6.0.1 → 6.1.0. Endor Labs can surface the level of impact and its potential breaking changes.
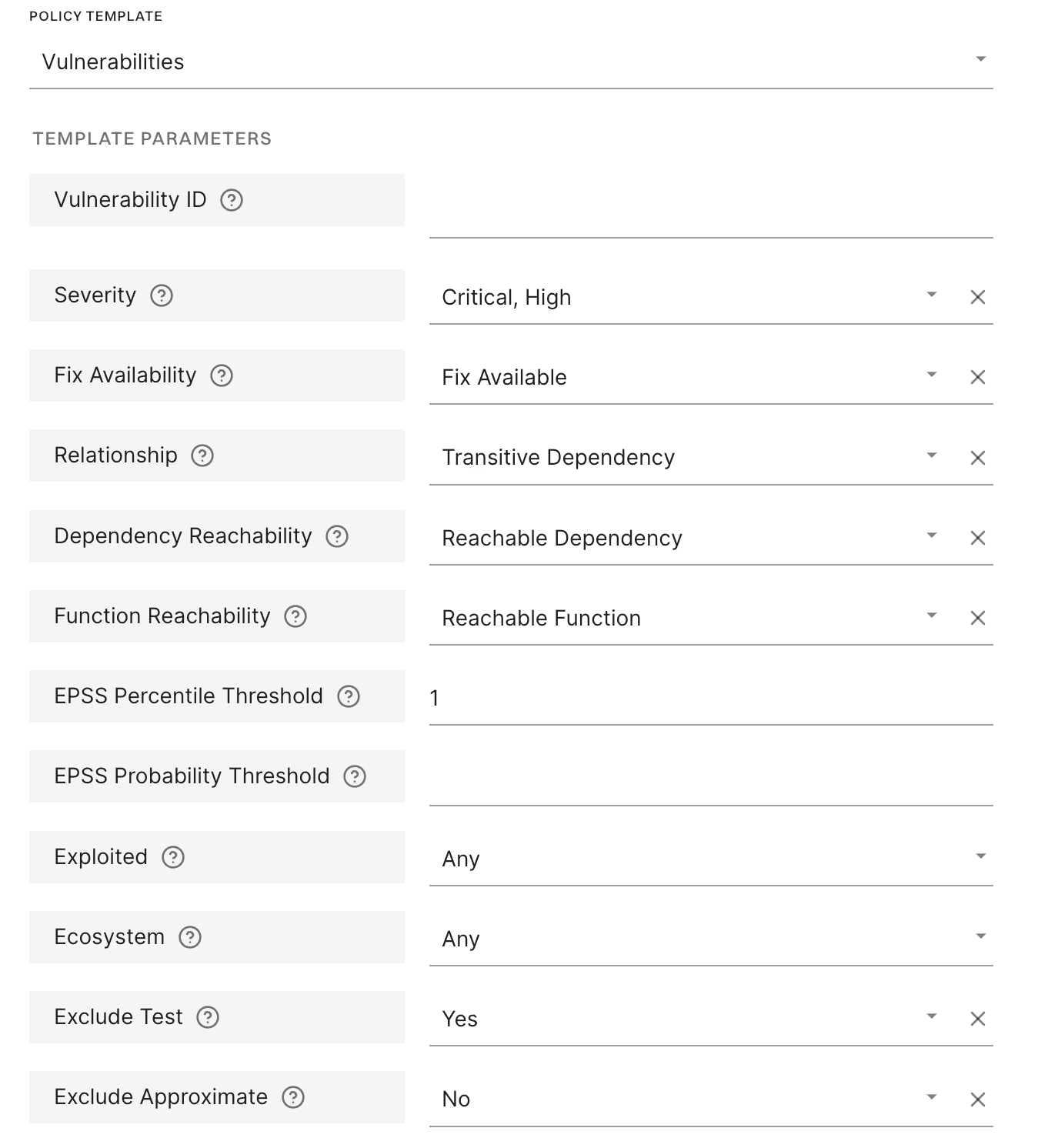
- Policy enforcement – If you gate builds on EPSS + reachability, today’s alert will show as informational rather than blocking, keeping pipelines green. The Endor Labs policy engine is highly customizable, so you if, for example, set a policy that only looks at reachability and not EPSS.
The bigger takeaway: context beats chaos
This incident is the textbook example of why raw CVSS scores don’t always equal real-world risk. Without context, a “critical” label can feel like a siren for nothing.
Modern AppSec is about filtering the noise so teams can focus on issues that truly threaten users and revenue. That means:
- Prioritize by exploitability – EPSS, reachability, and context cut 92% of the noise.
- Fix fast, but safely – Use upgrade-impact data or backported patches to remediate 6x faster
If you have questions about this CVE, Endor Labs customers can reach us at support@endor.ai.
Stay secure, ship fast — and keep calm when the next headline hits.
40+ AI Prompts for Secure Vibe Coding



What's next?
When you're ready to take the next step in securing your software supply chain, here are 3 ways Endor Labs can help:










